Unification vs. Diversity in Operational Technology Cybersecurity Design


In industrial environments, one of the key design considerations is whether to unify operational technology (OT) cybersecurity solutions under a single manufacturer or to utilize diversity across multiple vendors and products. Both approaches offer unique benefits and challenges that must be carefully balanced to achieve secure, reliable, and cost-effective system design.
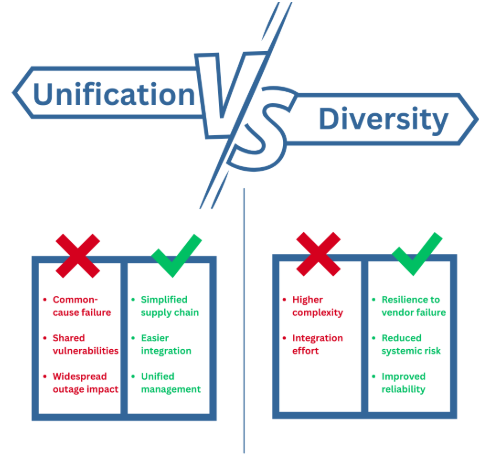
From a commercial and operational perspective, unification offers several advantages such as a single-vendor approach simplifies the supply process, standardizes design and configuration, minimizes integration challenges, and reduces the complexity of training, support, and maintenance, and also streamlines activities such as procurement, documentation, and lifecycle management, creating consistency across the organization by this unified approach can accelerate project execution and simplify post-deployment management.
When evaluated from a cybersecurity and reliability standpoint, full unification introduces notable risks particularly the risk of common-cause failure. If two redundant components (for example, firewalls) share the same model, firmware, and design, they also share the same vulnerabilities and failure characteristics. In such cases, if one component fails due to a software bug, misconfiguration, or cyber exploit, the redundant unit is likely to fail for the same reason. The result is that redundancy exists in design but not in function. This concept is well established in functional safety, where diverse sensors or controllers from different manufacturers are used to prevent a single design fault from compromising all protection layers. The same principle applies to OT cybersecurity; diversity reduces systemic risk and strengthens the overall defense posture.
A real-world example that highlights this risk is the CrowdStrike cyber outage, which affected multiple airports and organizations globally. The incident demonstrated how dependence on a single component or vendor can lead to widespread disruption, where one software error resulted in multiple system outages across critical sectors. In contrast, environments that implemented diverse solutions with different designs and third-party components experienced only partial impact or were entirely unaffected. This incident highlights the importance of designing systems that are not reliant on a single point of failure.
While diversity improves resilience, it also increases system complexity. Integrating solutions from multiple vendors requires additional effort in configuration, interoperability testing, and training. And redundant links and devices must be thoroughly tested to confirm proper failover behavior and to ensure that only one path or device performs a critical function at a time. These challenges, however, are outweighed by the improved reliability and robustness that diversity brings to the system.
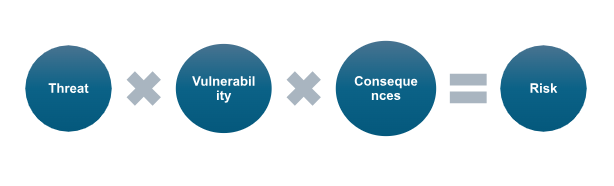
In cybersecurity terms, common-cause failure can be equated to ease of exploit, which directly increases the likelihood of compromise and consequently the risk. Therefore, a risk-based design approach should depend on diversity to reduce risk by design rather than relying solely on reactive protection measures. By incorporating diversity into the design phase, organizations can minimize the potential impact of unknown vulnerabilities and strengthen system resilience.
At CS4 by DTS Solution, we maintain multiple partnerships with leading cybersecurity vendors, enabling us to deploy each solution using different manufacturers and technologies. This approach supports diversity in design, which directly contributes to risk reduction while maintaining a balanced cost-to-security ratio. In addition, CS4 depends on diversity as a core design principle, ensuring that systems are inherently more reliable and secure against a wide range of risks. This philosophy allows CS4 to deliver architectures that achieve the optimal balance between security, reliability, and cost efficiency.
Diversity in the design of redundant OT systems not only enhances cybersecurity but also improves overall reliability against both intentional and unintentional failures. A well-balanced cybersecurity architecture is achieved by combining the operational efficiency of unification with the resilience benefits of diversity. Ultimately, investment in cybersecurity does not automatically translate to security. True security results from sound design principles, diverse protection layers, and the ability to maintain operation even under worst-case scenarios.
We offer comprehensive managed OT cybersecurity services through OT lifecycle.