CIE vs CCE – Two Powerful Approaches to Resilient Industrial Cybersecurity


Cybersecurity incidents in industrial control systems (ICS) and operational technology (OT) can lead to catastrophic safety, environmental, and operational consequences. Even with standards like ISA/IEC 62443 and secure development practices in place, we cannot guarantee that incidents won’t happen.
That’s why forward-thinking approaches like Cyber-Informed Engineering (CIE) and Consequence-Driven Cyber-Informed Engineering (CCE) have emerged. These methodologies embed cybersecurity into system design from the start, prioritize what truly matters, making system inherent secure, and complement existing standards to build resilience into critical infrastructure.
At first glance, CIE might seem like just another “secure-by-design” concept. But it is much broader and more strategic.
CIE integrates cybersecurity into every phase of a system’s lifecycle from concept and design through implementation, operation, and even retirement. Rather than treating security as an afterthought during deployment, CIE embeds it into the engineering process from the beginning by applying 12 guiding principles.
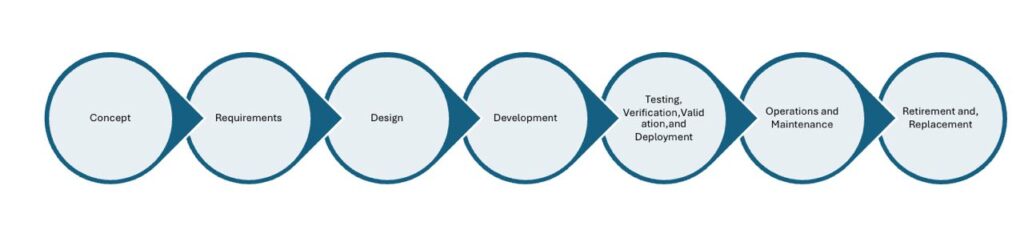
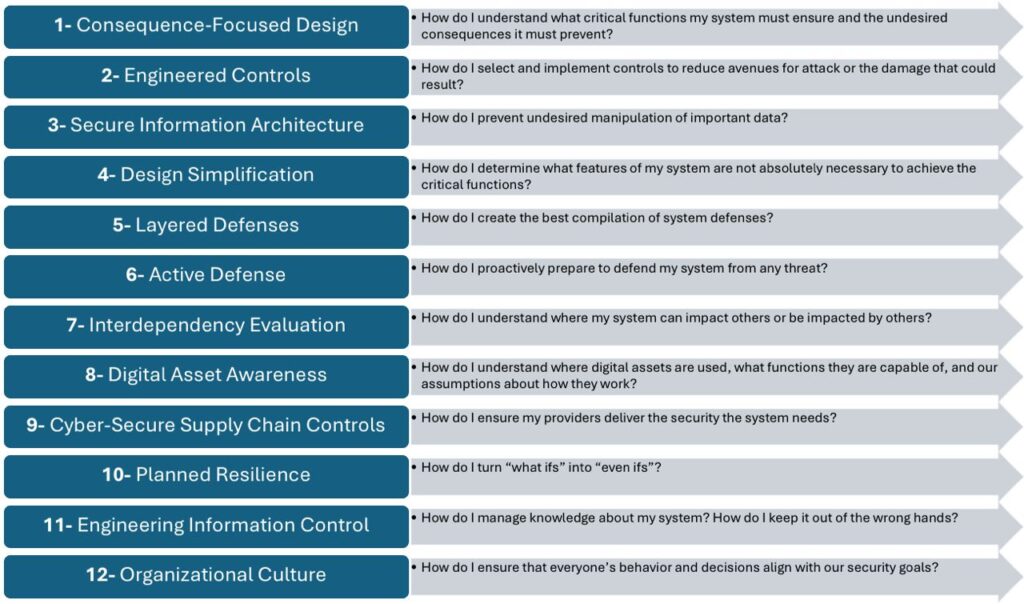
While CIE takes a broad, lifecycle-wide approach, CCE zooms in on what matters most the high-consequence events (HCEs) that could result in catastrophic outcomes.
Even with strong preventive controls, no system can guarantee 100% security. CCE acknowledges this reality and focuses on mitigating the consequences of inevitable incidents, prioritizing resources where failure would hurt the most.

While CIE and CCE are distinct, they are highly complementary.
In fact, CCE’s Phase 1: Consequence Prioritization directly informs CIE’s Principle 1: Consequence-Focused Design. Together, they create a continuous improvement cycle, CCE identifies what’s most critical, and CIE provides the engineering principles to protect it.
When mapped to the ISA/IEC 62443 standard, the distinction becomes clear:
– ISA/IEC 62443 emphasizes operations & maintenance, ensuring monitoring and controls after deployment.
– CIE & CCE emphasize the concept & design phases, embedding resilience from the start.
By combining CIE and CCE with ISA/IEC 62443, organizations can cover both proactive design and ongoing security management.
Both CIE and CCE represent a strategic evolution in industrial cybersecurity. They move beyond reactive controls and compliance checklists toward engineering systems that are:
One practical example: in designing a reactor, engineers applying CIE principles wouldn’t rely solely on a digital Safety Instrumented Function (SIF) to prevent overpressure. They would also include a mechanical pressure safety valve (PSV), ensuring protection even if the cyber-physical system failed.
In the complex and digital landscape of critical infrastructure, organizations can no longer rely solely on standards and reactive measures. CIE and CCE offer a powerful, integrated framework for building resilience into the very DNA of industrial control systems.
By identifying and prioritizing catastrophic consequences with CCE, and embedding security throughout the lifecycle with CIE, organizations can protect what truly matters from cradle to consequences.
We offer comprehensive managed OT cybersecurity services through OT lifecycle.